File Permissions in Linux
One of the most essential aspects of the Linux operating system is file
permissions: they determine how users on the system can interact with
the various files available on it, which are a basic function of any
operating system.
Especially for beginners, this concept is not that easy to grasp as well
as very general and detailed to be a side-note in any post — so this is
the answer to the call: this article will explain this crucial subject
in depth.
Why are permissions even necessary?
At
first thought, we might consider completely abolishing the idea of
permissions. Why complicate things? Let’s just let everyone have access
to everything, and explain the users of the system what are their
constraints and provide guidelines of usage. Sounds easy, right?
But
this attitude is prone to many problems. First of all, we humans tend
to mistake. A lot. This is natural, but the potential problems are too
risky for us to just cope with them — maybe we destroy a configuration
file for a program or corrupt an important file. We can’t just hope for
the best — we need to actively protect ourselves and avoid such issues.
Nevertheless,
the biggest problem resides in the field of information security. An
attacker acquiring access to the system is a big issue for itself, and
significantly worse if he could do whatever he wants with any file — we
should keep in mind that enterprise machines contain many sensitive
pieces of data, and the potential for vital, dangerous problems is huge.
Do these comprise enough reasons for us to utilize a system managing
access permissions?
I
hope you are convinced in the need for such system. The developers of
the Linux OS certainly are, so let’s dive in and explore the subject.
Understanding file permissions
When we open our terminal, we are presented with a shell and located in a particular directory. By executing the ls command, we can view the files in the mentioned directory.
For demonstration purposes, let’s navigate to the /etc directory, inside which there are both files and directories.
Using the ls command without parameters simply show
the available files and folders (the white are files, the blue are
directories, and the light-blue is a different concept we’ll briefly
touch later, called a link). For us to see the permissions of the various entries, as well as many other relevant details, we need to add the -l parameter:
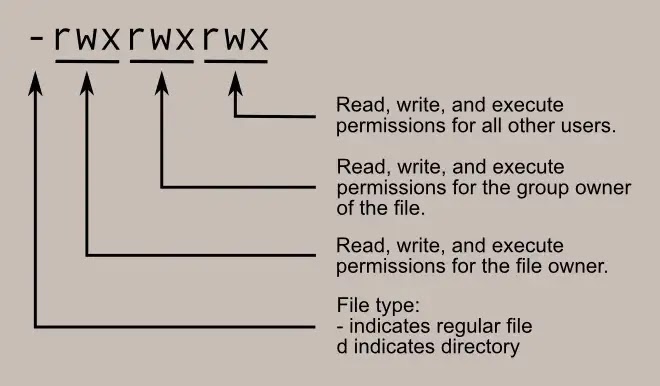
The first group of letters are the heart of this article, we’ll focus on them. The number after them is the amount of links
to the file/directory, the name after it is the owning user, followed
by the group of the owning users (users in Linux are divided into
logical structures called groups. A user can be a part of more than a
single group). Next, the number represents the size of the file in
bytes, after which we have the time of last modification, followed by
the name of the file/folder.
As
I said, we’ll take a look at the group of letters on the left. The
first one is either “-”, “d” or “l”. “-” mentions a file, “d” is a
directory, and “l” is a link. So far, so good. Now things become more
interesting.
The
remaining letters actually comprise 3 groups of 3 letters: “r”, “w”,
“x”. The first group describes the permissions of the user who owns the
file, the second group describes the permissions of the owner’s group,
and the third describes the permissions for any other user on the
system. It’s worth mentioning that the root user has full access to any file, and can do whatever he wants.
Now
we’ll understand how permissions are specified by the 3 mentioned
letters — and the concept is the same for the user, group and other
users. Each letter represents a permission: the “r” stands for reading
the file, the “w” stands for writing to the file, and the “x” stands for
executing the file, running it as a program. The sequence “rwx” gives
full permissions, whereas if a particular permission is denied, the
pertinent letter would be substituted by a dash “-”. For instance, “r-x”
allows reading and executing, and “- -x” allows execution only.
For example, let’s take a look at the sequence “-rwxr-xr- –”.
Because it starts with a “-”, it means it is a file. The next group of
letters is “rwx”, providing the owning user with full permissions. As
opposed to him/her, the users of the same group cannot write, but only
read and execute (“r-x”). Other users can only read the file (“r- -”).
The equivalent for directories
Permissions
of directories differ a bit from those regarding files. If a given
sequence of letters is pertinent to a directory, but not to a file, the read permission allows examining the contents of the directory, seeing what files are inside it — basically, performing ls. The write
permission makes it possible to create, rename or delete a file in the
relevant directory, as well as altering the attributes of the directory.
The execute permissions determines whether it is possible to enter the folder, basically cd into it.
Changing permissions
Only the root user or the owner of the file can alter the access permissions of the file.
To update the permissions of any given file or directory, we utilize the chmod
command. There are 2 ways of doing so: numerically and with
alphabetical expressions. Let’s start by the numerical method. In this
method, every permission is assigned to a number: read = 4, write = 2, execute = 1.
The numbers are not random, but are the values of the first three bits
in the binary representation. Notice that there cannot be two
combinations (let alone more) of permissions whose sum is identical. In
this way, we can specify the permissions:
chmod 644 file
The
first number sets the permissions for the user, the second number is
pertinent to the group, and the last one is for other users. This
statement says that the user has reading + writing (4 + 2 = 6), whereas
any other user, no matter what group s/he’s in, has only writing
permissions. To allow full access to any user, we can type:
chmod 777 file
Since reading + writing + executing = 7 (4 + 2 + 1 = 7).
Now
let’s scrutinize the alphabetical expressions. In this attitude,
instead of the digits, we type: {who}{+ or -}{what permission}. For
instance:
chmod u+x file
The u indicates the user, and we add the execution permission to him/her. Another example:
chmod g-w file
The g indicates the group, and we remove the writing permission from it. “Other users” are described by the letter o, and reading permission is tied to the letter r.
A little debt — what links are
We
saw before that apart from files and directories (folders), we also
have links. Basically, links point to another file, providing a way to
reach it from a different place. There are hard links
— which are files standing for themselves, pointing into the same
location on the hard disk as does the file to whom they are linked. As
opposed to them, we have soft links, that
are not files standing for themselves, but point to the location in the
file system where the linked file is located. This is a very
interesting subject, and I recommend you take a deeper look into it on
your own.
Real-world example of protection provided by file permissions
Imagine
you are a simple user in an organization, reckless and carefree. A
malicious person succeeded in laying a hand on your credentials, and
logs into the system with them.
This
for itself is a significant breach, but thanks to file permissions, the
damage is relatively mitigated. As a simple user, you don’t have access
to sensitive data, and you cannot read the passwords file, for example.
Deriving from that, so would the attacker not be able to do so, and the
damage s/he can cause is limited.
Moreover,
even if the attacker planned to corrupt the system by editing
particular files or executing a dangerous script, a wise setting of
permissions will block this offensive vector as well.
This
way, until the breach is discovered and dealt with, there would be no
crucial issues caused. Thank God and the Linux file permissions.
Conclusion
We learned the most important concepts and aspects of file
permissions in the Linux OS (and yet, it is not all there is to know),
such as: the various access permissions and their meaning, for both
files and directories, why they are important, how to change them, how
to check them, the separation between the owning user, his group and
other users on the system, and more.
For
any user of Linux, it is vital to comprehend file permissions and know
how to use them. They are utilized in many fields, especially in
Information Security.
Thank you!